As with any cluster, there is a master/slave relationship and there is no difference with CMS DB Clustering. We first need to initialise the DB Master, followed then by connecting all DB slaves. Remember.. The CMS DB Cluster must have an ‘odd’ number of members.. Another note to make about cluster members is the Call Bridge doesn’t have to be operational.. Hence DB Cluster members can be on general/standard VMs with typical resource usage such as CPU and Memory.. No need to allocate huge amounts of resources to DB Cluster members.. One example I can give is to have a 2 node Call Bridge Group configured linking to a 3 node DB Cluster.
Configuration steps starting with the CMS Database Master
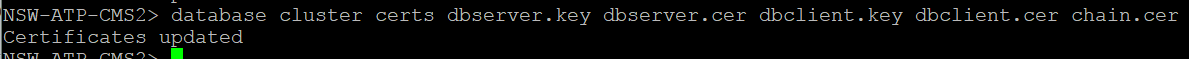
Attach certificates to the database cluster.. We have already provides CSRs and have signed certificates from previous steps.
From the console enter:
database cluster certs dbserver.key dbserver.cer dbclient.key dbclient.cer chain.cer

database cluster localnode a (We are specifying the CMS network interface for the DB to use)
Now Join each of the Slave Database Servers to the database cluster
Upload via SFTP the below certificate files
- Dbserver.key
- Dbserver.cer
- Dbclient.key
- Dbclient.cer
The above files were generated under the Certificates section. These files will be shared among CMS Servers.
Validate the certificate files on the CMS Server via the ‘pki list’ command
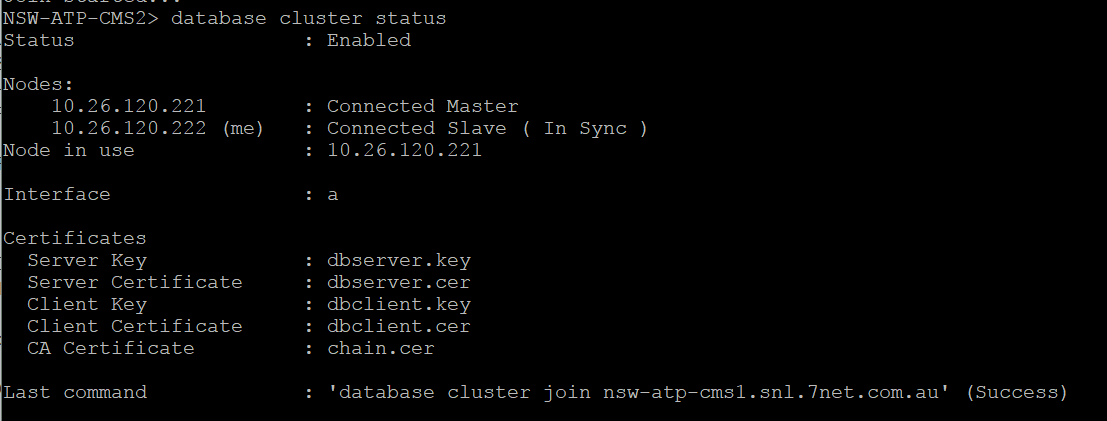
database cluster certs dbserver.key dbserver.cer dbclient.key dbclient.cer chain.cer

database cluster localnode a
database cluster join cms_hostname.com.au (this is the DB Master’s hostname)

Repeat for each Slave Database Server. Note: Do not have an equal number of Database Servers in the cluster, must have odd number count. Example Cluster of 3 or 5 not 2 or 4.