As most of you know the Cisco IPSEC VPN Client is not officially supported on Windows 8+. I have Window 10, now that puts me in the not so friendly basket. After googling this, there a raft of blogs and websites advising you to install additional components and modify registry settings.. Not all of which are proven. I finally found a sequence that worked for me.. AND successfully connected to customer sites.
First thing is to get around this virtual adapter filter thing that doesn’t get installed with Windows 10.. The SonicWall VPN Client however does install the ‘DNE Lightweight filter network client’. Beautiful.. Job done.
Link to Sonicwall website for vpn client. http://help.mysonicwall.com/applications/vpnclient/
If the above link is not available and you cannot find it anyway.. Ping me and I’ll email it to you.
Right. Lets install the Cisco IPSEC VPN Client now.. No wait another error.. ‘This software doesn’t support Windows 10′, great. To get around this one.. Extract the install files and manually run the .msi file. Job done.
Now the client is installed and we are away and running.. Try to connect to a customer site and low and behold another error.. ‘Secure VPN Connection terminated locally by the client. Reason 442: Failed to enable Virtual Adapter.’ we are getting closer though right?
Here comes the infamous registry change.. Now I’ll add the general blurb that everyone would say… ‘Backup your registry settings in case you absolutely blunder this change’. Now lets get started.
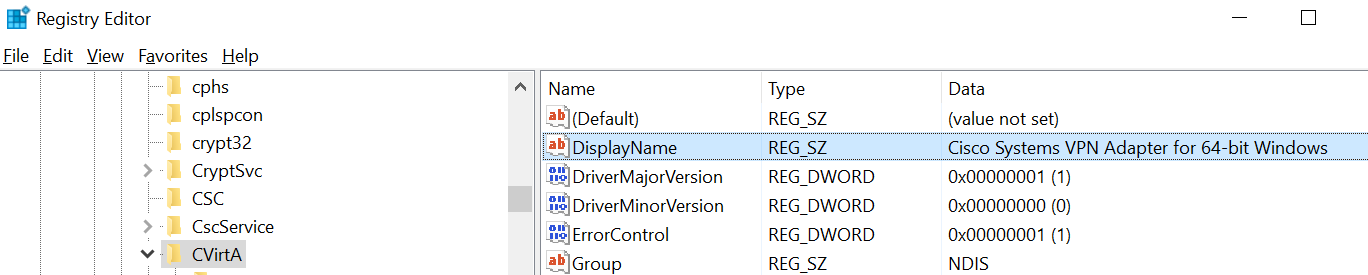
Open registry and go to HKLM\SYSTEM\CurrentControlSet\Services\CVirtA look for the key ‘Display Name’. We want to modify this key from something like this ‘@oem47.inf,%CVirtA_Desc%;Cisco Systems VPN Adapter for 64-bit Windows‘ to ‘Cisco Systems VPN Adapter for 64-bit Windows‘ (screen shot below of change).
Now open the VPN Client again and try connecting to a customer site.. Whola! Job is now done. Thanks Internet.