Quick note on deploying/renewing certificated for clustered expressway devices, whether it be EXP-C or EXP-E devices. Typically, you will want the same SAN Certificate loaded onto each Expressway device. Outlined below is the process to deploy a single SAN certificate for each node in the cluster.
Primary Node Certificate Deployment
Follow the recommended certificate generation process for the first Expressway node. Generate a CSR on primary Expressway, ensuring to include cluster name and all peer names. Add additional names into the CSR as required. Typically you will need the domain name for MRA and “Join” FQDN for CMS WebRTC.
Have the CSR signed by a public CA. (or Internal in the case of an Expressway-C Device). Download the Server Certificate and Chain.
Install the chain certificates first onto each Expressway Node, then install the server certificate onto the Primary Expressway-E. A reboot is required to complete the process.
Using the same certificate for the secondary and remaining cluster peers.
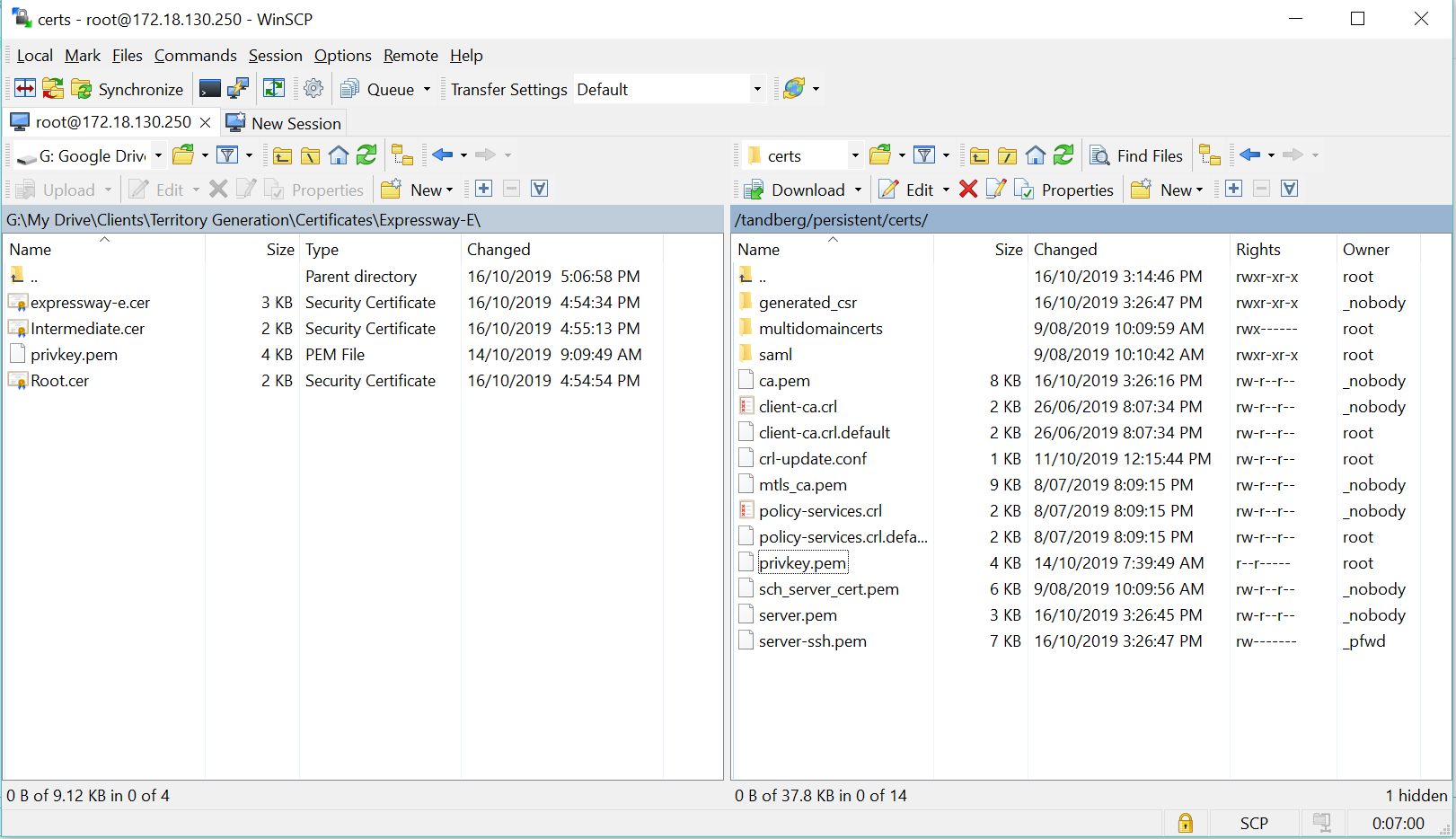
Using WinSCP, log into the Primary Expressway-E device using the root account.
Navigate to the directory Persistent>certs and copy/download the file ‘privkey.pem’. This is the Private Key.
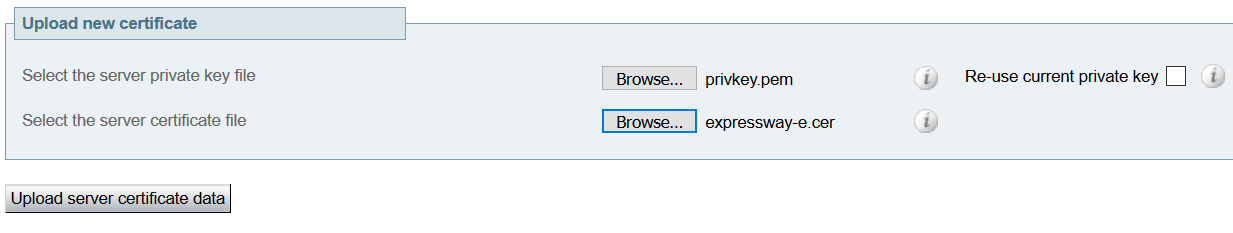
Log into the Secondary Expressway-E nodes and upload both the Private Key and Server certificate together. (As mentioned above, ensure the Chain Certificates have already been uploaded.)
Repeat for each additional Cluster Peer.