Cisco Meeting Server provides a more feature rich conference environment with Active Control enabled. Not only the does the CMS Server need the SipUDT flag enabled (enabled by default), the Call Leg Profiles needs to have the feature enabled, the codecs need meet firmware versioning minimums and have the Active Control flag set to Auto as well as CUCM will need to have the relevant SIP Profiles sending the Xi Parameter for Devices and Trunks. Tracing Active Control is done via SIP and Active Control XCCP Packets, I’ve outlined below some key components to tracing Active Control Features. Below is an example of the Codec Muting and Unmuting itself. The unmuting will reflect the change in the rxAudioMute flag on the CMS Server, which is turn reflects the Microphone Unmuting in the CMM Management Screen. Also, worth to note, the below output is also based on ‘Linked’ Mute Behaviour as opposed to ‘Separate’ Mute Behaviour.
Scenario:
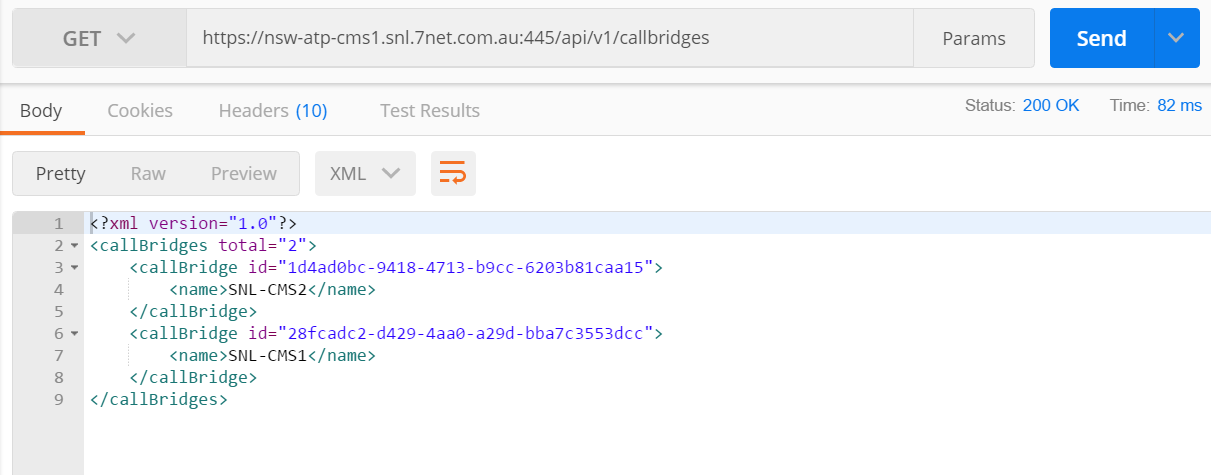
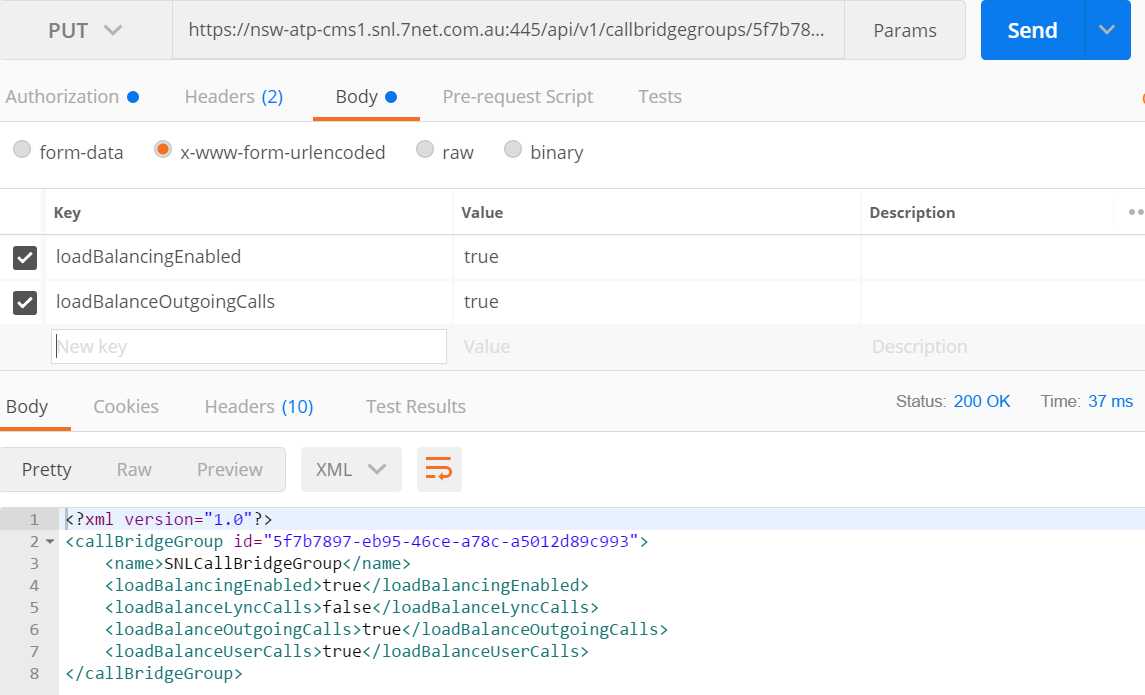
- Multiple Call Bridges in a single Call Bridge Group with Load Balance enabled
- Cisco SX20 Codec operating 9.15.X firmware.
- Call Bridge version is 3.2.1
- CUCM version 14 SU2
- Direct routing between CUCM and CMS
- Call Leg Profile is set as below
- rxAudioMute = True (Mute on entry)
- muteSelfAllowed = True (Allow Codec to unmute/mute as required)
Call Flow:
Codec -> CUCM -> CMS -> CMS
Codec dials into Space directly, CUCM sends a Delayed Offer to the landing point is which is CMS01. Load Balancing is then conducted, CMS02 Call Bridge is voted to host the conference. CMS02 then places an outgoing call to the Codec, hence sends a SIP INVITE to the CUCM. CMS01, will CANCEL the original SIP INVITE from the Codec/CUCM.
So, the within the SDP, there should be a couple of attributes to the tune of..
m=application 30419 UDP/UDT/IX *
a=ixmap:0 ping
a=ixmap:2 xccp
This is the Active Control negotiation within the SDP. If these lines are not present, then CMS is not enabled for Active Control. Vise versa.. If CUCM sends the 200 OK SIP Msg without the above attributes, then CUCM Sip Profiles do not have Active Control configured.
Active Control Tracing on the CMS will not show the Active Control State of the call via the b following line ‘ActiveControlState change, unknown -> negotiating’.
<?xml version=”1.0″ encoding=”UTF-8″?>\n
TX: <request type=”subscribe-capabilities” id=”1″>\n
TX: <subscribe-capabilities min-interval=”5″>\n
TX: <expires>1800</expires>\n
TX: </subscribe-capabilities>\n
TX: </request>\n
call 4942: need to start new conferencing link for XCCP
call 4942: starting up conferencing link for XCCP
call 4942: starting up conferencing link user for XCCP
call 4942: incoming XCCP message, size 197:
RX: <?xml version=”1.0″ encoding=”UTF-8″?>\n
Active Control Feature and Capabilities will now be negotiated between the CMS Call Bridge and the Codec.
CMS Call bridge will not set the feature capabilities upon the Codec. Below snippet is the Call Leg Parameter ‘rxAudioMute’ being pushed down to the Codec. (Also, within this same xml msg, the parameter ‘rxVideoMute’ is also pushed down to the Codc)
call 4942: outgoing XCCP message, size 684:
TX: <?xml version=”1.0″ encoding=”UTF-8″?>\n
TX: <notify type=”acked-self-info” notifyId=”4″>\n
TX: <self-info>\n
TX: <user id=”e0d5c105-5b68-44bd-85a6-3c3b2f23a749″ entity=”91021@justice.nsw.gov.au”>\n
TX: <display-text>SYD-DOWN-MULTIMEDIA-MR1- 91021</display-text>\n
TX: <recording>false</recording>\n
TX: <deactivated>false</deactivated>\n
TX: <endpoint entity=”91021@justice.nsw.gov.au”>\n
TX: <status>connected</status>\n
TX: <joining-method>dialed-out</joining-method>\n
TX: <capture-source-id>19416111</capture-source-id>\n
TX: <media id=”1″>\n
TX: <type>audio</type>\n
TX: <status>recvonly</status>\n
TX: </media>\n
TX: <media id=”2″>\n
TX: <type>video</type>\n
TX: <status>recvonly</status>\n
TX: </media>\n
TX: </endpoint>\n
TX: </user>\n
TX: <count>\n
TX: <visible>0</visible>\n
TX: </count>\n
TX: </self-info>\n
TX: </notify>\n
At this point, the Codec has successfully joined the Conference, the Call Bridge has set the relevant features upon the Codec. The Codec has been Muted both Audio and Video.
The Meeting Room Operator, can now press the Mute Button on either the Touch 10 or an external Microphone to unmute the Codec. Below is snippet for the XML Msg sent to the Call Bridge from the Codec.
call 4942: incoming XCCP message, size 225:
RX: <?xml version=”1.0″ encoding=”UTF-8″?>\n
RX: <request type=”self-mute” id=”7″>\n
RX: <self-mute>\n
RX: <endpoint entity=”91021@justice.nsw.gov.au”>\n
RX: <media id=”1″ media-allowed=”sendrecv”/>\n
RX: </endpoint>\n
RX: </self-mute>\n
RX: </request>\n
The Call Leg parameter ‘rxAudioMute’ is not set to false and the CMM Server will indicate the Mute is now off from the Codec.
Further Notes to Muting/Unmuting behaviour with Active Control. The CMM Server cannot unmute the Codec. If you attempt to unmute via CMM Console, the microphone icon will switch off for a couple of seconds, then switch back on indicating the microphone is muted again.